
Cyber Forensics 4 ALL is an online cloud-based education platform that aims to enhance students’ learning experience in the field of Computer Forensics and Digital Evidence. Our goal is to educate students on the nuances of this field while making the learning experience better. By simulating well-known, real-world incidents involving criminal activity and the accompanying cyber investigations, we have provided case studies that will provide a contextual-based, online-learning environment. We also strive to help the law enforcement study the incidents and provide more efficient ways to carry out the forensic investigations.

Attackers exploit Fortinet flaws to deploy Qilin ransomware
June 6, 2025
Qilin ransomware now exploits Fortinet vulnerabilities to achieve remote code execution on impacted devices. Threat intelligence firm PRODAFT warned that Qilin ransomware (aka Phantom Mantis) group targeted multiple organizations between May and June 2025 by exploiting multiple FortiGate vulnerabilities, including CVE-2024-21762, and CVE-2024-55591. “Phantom Mantis recently launched a coordinated intrusion campaign targeting multiple organizations between […]
Read Full Article
Russia-linked threat actors targets Ukraine with PathWiper wiper
June 6, 2025
A Russia-linked threat actor targeted a critical infrastructure organization in Ukraine with a new destructive malware dubbed PathWiper. Russia-linked threat actor targeted Ukraine’s critical infrastructure with a new wiper named PathWiper. Cisco Talos researchers reported that attackers utilized a legitimate endpoint administration tool, indicating they had access to the administrative console, then used it to […]
Read Full Article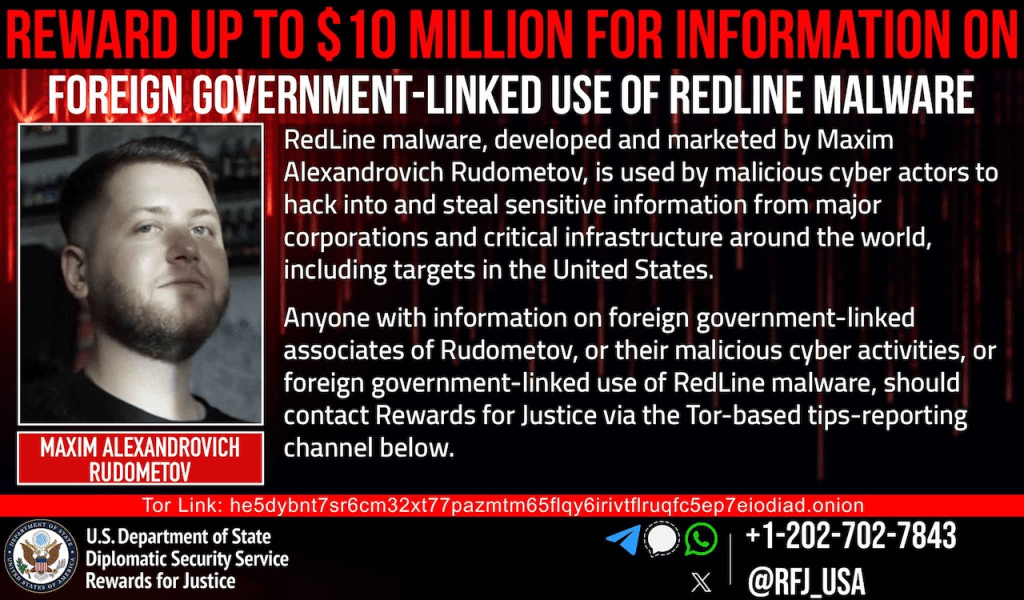
U.S. Offers $10M bounty for info on RedLine malware creator and state hackers
June 6, 2025
The U.S. offers up to $10M for info on state hackers linked to RedLine malware and its creator, Maxim Rudometov, tied to attacks on U.S. infrastructure. The U.S. Department of State offers a reward of up to $10 million for information nation-state actors linked to the RedLine infostealer and its alleged author, Russian national Maxim […]
Read Full Article
Play ransomware group hit 900 organizations since 2022
June 6, 2025
A joint advisory from the US and Australian authorities states that Play ransomware has hit approximately 900 organizations over the past three years. A joint advisory from the Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), and Australian Signals Directorate’s Australian Cyber Security Centre (ASD’s ACSC) states that Play ransomware has hit […]
Read Full ArticleHello, Has anyone here secured any forensic related internships for 2024? I'm collecting some data and wanted to know what kind of companies are hiring interns and what the process...
By AP Malla, 1 year ago





